A new family of iOS malware that is able to infect non-jailbroken iOS devices without relying on an enterprise certificate has been discovered by Palo Alto Networks.
Dubbed “AceDeceiver,” the malware is able to infect iOS devices by exploiting flaws in FairPlay, Apple’s DRM (digital rights management) system.
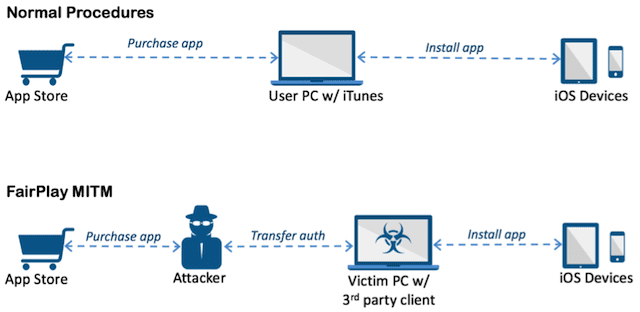
According to Palo Alto Networks “AceDeceiver is the first iOS malware we’ve seen that abuses certain design flaws in Apple’s DRM protection mechanism — namely FairPlay — to install malicious apps on iOS devices regardless of whether they are jailbroken. This technique is called ‘FairPlay Man-In-The-Middle (MITM)’ … Apple allows users purchase and download iOS apps from their App Store through the iTunes client running in their computer. They then can use the computers to install the apps onto their iOS devices. iOS devices will request an authorization code for each app installed to prove the app was actually purchased. In the FairPlay MITM attack, attackers purchase an app from App Store then intercept and save the authorization code. They then developed PC software that simulates the iTunes client behaviors, and tricks iOS devices to believe the app was purchased by victim. Therefore, the user can install apps they never actually paid for, and the creator of the software can install potentially malicious apps without the user’s knowledge.”
Three different apps claiming to be wallpaper apps, but in actuality were a part of the AceDeceiver family, were uploaded to the official App Store between July 2015 and February 2016. These apps provided attackers with a fake authorization code.
A Windows client called “Aisi Helper” was installed by users in China, and installed malicious iOS apps on the devices.
The apps have been removed from the App Store by Apple, but remain a threat because attackers still have authorization codes needed to install fake apps.
As of now, only users in China are maliciously affected by AceDeceiver, but Palo Alto Networks states that this could change at any time.
Palo Alto Networks has offered this advice for users: “We suggest users who installed Aisi Helper’s Windows client or iOS apps after March 2015 to remove these software and apps immediately, as well as change their Apple ID passwords. We also suggest all iOS users to enable two-factor authentication for their Apple IDs.”
For more information, you can read the entire Palo Alto Networks report here: researchcenter.paloaltonetworks.com/2016/03/acedeceiver-first-ios-trojan-exploiting-apple-drm-design-flaws-to-infect-any-ios-device/