 Over the next few weeks, Rocket Yard is treating you to a series of articles about networking and security. We’ll cover a variety of topics, beginning today with a primer on DNS (Domain Name System). DNS is an essential component of the Internet; it’s not a stretch of the imagination to say that without DNS, today’s Internet would not be possible.
Over the next few weeks, Rocket Yard is treating you to a series of articles about networking and security. We’ll cover a variety of topics, beginning today with a primer on DNS (Domain Name System). DNS is an essential component of the Internet; it’s not a stretch of the imagination to say that without DNS, today’s Internet would not be possible.
What Does DNS Do?
To put it simply, DNS associates the numerical IP addresses (like 67.176.63.30 (IPv4) or 2600:1005:b062:61e4:74d7:f292:802c:fbfd (IPv6)) of network-attached devices with domain names assigned to an entity. If it wasn’t for DNS, we’d all have to remember those numerical addresses instead of just typing in a memorable name like “rocketyard.com”.
DNS was designed from the start to be distributed, meaning that copies of parts of the DNS database are stored in many places. This makes the system fault tolerant, since a failure of one DNS server cannot take the entire system down. Likewise, it makes the size of the DNS database manageable by avoiding a single large central database.
As an example of how DNS works, let’s think about how you got to the Rocket Yard. You pulled up a web browser on your Mac, iPhone or iPad, then typed in the address https://rocketyard.com and pressed Return. Your device then issued a query to a DNS server, most likely one run by your Internet Service Provider (ISP). To make things easier, the queries are usually done iteratively, passing along a DNS request to one or more server. With our example of the Rocket Yard, we’d resolve the address perhaps with a global root name server (there are just 13 of these), then a server that just holds part of all of the “.com” addresses, a name server that knows the rocketyard.com address, and finally the eshop.macsales.com/blog address that is at the core of this website.
That numeric IP address is then returned to your Mac, and a network connection is made between the two numeric IP addresses — one for your computer, the other for the Rocket Yard. At that point, your web browser can “converse” with the macsales.com web server, and you can read this article or perhaps buy a memory upgrade kit.
The diagram below (from KeyCDN.com) shows a typical query to the domain name server to obtain the IP address, then a direct connection to the web server to view a web page:
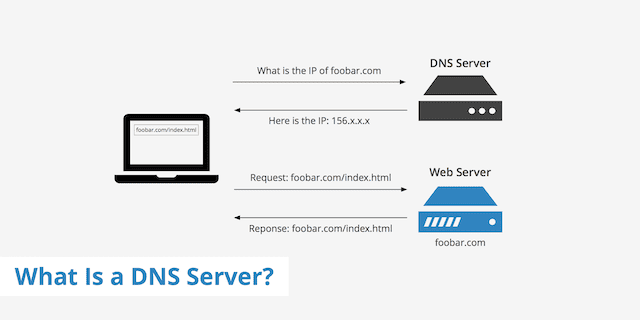
Authoritative Name Servers and DNS Records
When a company or person registers a domain name through a domain registrar like GoDaddy, Network Solutions, or DreamHost, the registrar starts by assigning that domain name to what is called an authoritative name server. For redundancy purposes, each domain name is usually listed with more than one whois name server, for example ns1.myhostingcompany.com, ns2.myhostingcompany.com, etc… These are the authoritative name servers for the domain.
These servers are sometimes referred to as “whois” name servers. “Whois” refers to an Internet service that lets users find out who owns a particular domain name or where it is hosted.
Through a control panel or command-line interface, it’s possible for webmasters and network administrators to add different records to the DNS information for a domain name. Each of these records has a specific type and value. While there are many different DNS record types (around 40 are in use), the most common are:
- A – The address record, which maps the hostname to an IP address. An “A” type record will have a value of something like 63.163.164.241 (or an IPv6 equivalent). Services that are associated with a domain name, like “www” for a web server, “ftp” for a file transfer protocol server, “mysql” for a mySQL server, or “ssh” for a secure shell server, will all have individual records and may have different values or IP addresses associated with them.
- CNAME – A canonical name record. “CNAME” records are most often used as an alias to another address. For example, one web server might use an external service to run an online store that’s located a server other than the web server. A typical CNAME record in this case might show the record “store” and a value of “store.onlinestores.net”, so that when someone tries to go to “store.rocketyard.com” they are directed to the third party provider at “store.onlinestores.net”.
- NS – The name server record, which delegates a DNS zone to an authoritative name server. The “NS” type record usually has a value that looks something like “ns1.myhostingcompany.com”. There are as many NS records for a domain name as there are authoritative name servers assigned to the domain name.
- MX – Mail exchange records. These map a domain name to message transfer agents (otherwise known as mail servers) for the domain. MX records are extremely important as they are used by mail servers to exchange messages. A domain can have many MX records, each of which points to a different mail server for the domain.
- TXT – Text records containing either text or machine-readable data. A common use for “TXT” records is to allow Google Analytics to verify that a person in authority is behind a request to connect a website to the analytics service. In this case, the value is something like “google-site-verification=Mabc-Glr6FTWWoMOviop14ZjdPtm6xoXfY6vhiLq8VI”
Top-Level Domains
We talked about domain names earlier – rocketyard.com is a perfect example of one of those. The second part of the domain name – the “dot com” – is referred to as a top-level domain or TLD.
Originally, there were just a few TLDs: .com, .net, .edu, .gov, .org, .us, .uk and so on. Over the years, the Internet Corporation for Assigned Names and Numbers (ICANN) has added more TLDs. There are over 290 country code top-level domains, plus more verbose TLDs like .museum, .today, .travel, .bargains, and a lot more.
These new TLDs give webmasters a lot more flexibility in creating web addresses. Have a website that sells cheap airline tickets? You could register the domain name “GetYourCheap.Flights” for your company.
Security Issues With DNS
Like just about everything else on the Internet, DNS can be used by malicious parties to cause issues – usually sending unsuspecting users to “fake” websites that appear to be real.
One way that hackers take advantage of DNS is through what’s called DNS cache poisoning. Each DNS record has what is called a TTL – time to live. That’s the number of seconds that the resource record remain valid. Hackers distribute data to resolving servers that cache the resource record information, adding false information and IP addresses. A request to go to a specific web site is then redirected to a malicious website, usually for the purpose of stealing personal information from an unsuspecting user.
A much easier way is to spoof domain names so that they look like trusted domain names. An example would be creating a website with the name paypa1.com, making it look like the PayPal website. A user could be directed to the bad address through a link in a phishing email, yet when they look at the address in their web browser, they see paypa1.com – which looks a lot like PayPal.com.
One very common and serious DNS-related event is what is called a Distributed Denial-of-Service or DDoS attack. These are attacks on one or more of the thirteen DNS root nameserver clusters and can cause very bad problems as these clusters are perhaps the most critical infrastructure of the Internet. In theory, a prolonged attack hitting all of the root name servers could take down the entire Domain Name System and all Internet services that use it. The following image from AVG provides a visual explanation of how the attacks occur.
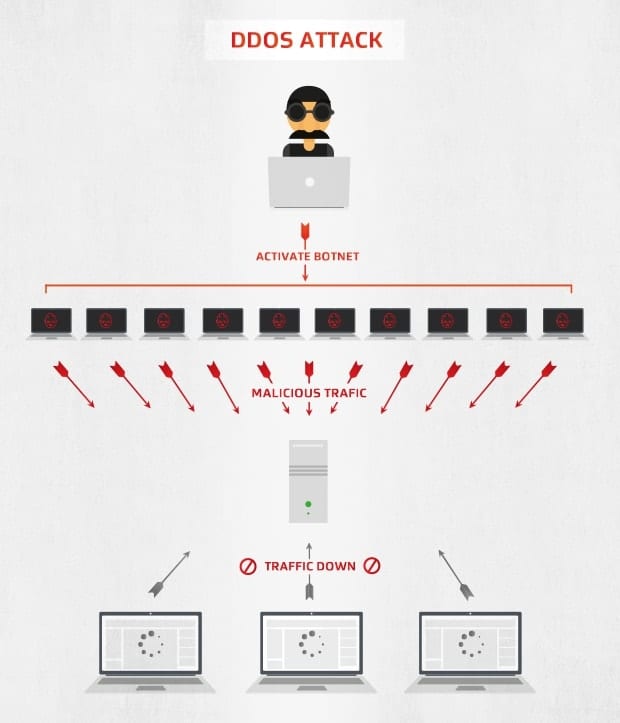
How do malicious parties perform a DDoS attack? They try to overwhelm the server with a flood of internet traffic. It’s basically akin to sending a lot of cars onto a freeway in a deliberate attempt to create a traffic jam that shuts down a city. To do this, a malicious party must have a lot of computers and other devices under their control that can be set up to make repeated queries to the root nameservers at the same time. The devices are usually infected with malware that turns them into an unwilling “bot” or “zombie” that has one task — send a request to the target IP address. The attacker has control over this fleet of bots (otherwise known as a botnet), and can send instructions such as the target address and time of attack to all of the bots.
Fortunately, DDoS attacks are relatively rare. Many of the organizations that control the root name server clusters have plans in place that can mitigate the effects of an attack by first detecting that an attack is underway, blocking what appears to be bot traffic, routing traffic elsewhere to prevent denial-of-service, and adapting to attacks through AI.
There’s a lot more to learn about the Domain Name System. A very good online resource to educate yourself about DNS is available from Cloudflare.








“Fortunately, DDoS attacks are relatively rare.” Really?
https://threatmap.checkpoint.com/ThreatPortal/livemap.html
https://www.fireeye.com/cyber-map/threat-map.html
https://cybermap.kaspersky.com
https://www.digitalattackmap.com/#anim=1&color=0&country=ALL&list=0&time=18033&view=map